What is ProxyNotShell Attack?
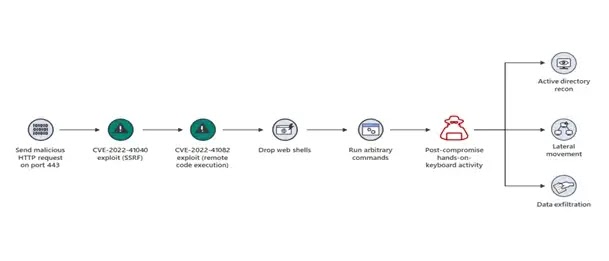
The ProxyNotShell vulnerability is a critical security flaw that was discovered in Microsoft's Exchange Server. This vulnerability is categorized as Server-Side Request Forgery (SSRF) and has been assigned the CVE-2022-41040 identifier with a CVSSv3 score of 6.3. In addition to this, there is another vulnerability that has been categorized as remote code execution (RCE) with the CVE-2022-41082 identifier and a CVSSv3 score of 8.8. These vulnerabilities pose significant risks to users and should be addressed as soon as possible.
Where was it Found?
The ProxyNotShell (CVE-2022–41040) vulnerability was discovered in the Microsoft Exchange server on September 29, 2022. At that time, Microsoft confirmed reports of adversaries exploiting two zero-day vulnerabilities that affected the Exchange service. In August 2021, around 1,900 Microsoft Exchange Servers were known to have been hacked. Many organizations were affected by ProxyShell attacks, including construction companies, food processors, industrial machinery manufacturers, repair shops, and even a small residential airport, according to Kyle Hanslovan, CEO of Huntress Labs. These vulnerabilities pose significant risks to users and should be addressed as soon as possible.
What all can it do?
The ProxyNotShell (CVE-2022–41040) vulnerability allows attackers to plant ransomware and gain access to critical files on the Exchange mail server by exploiting the vulnerability to perform remote code execution. This vulnerability is particularly easy to exploit, making it a significant threat to organizations. To help organizations assess their level of exposure to ProxyNotShell, Cymulate Research Lab has developed a custom assessment tool that can be used to estimate the level of risk. It is important for organizations to use this tool or other means to assess their exposure to this vulnerability and take steps to address it as soon as possible.
Ways to Exploit CVE-2022-41040:
nmap --script proxyshell.nse your target -p 443
you can also use the Metasploit framework to exploit the ProxyNotShell (CVE-2022-41040) vulnerability.
To use Metasploit to exploit the ProxyNotShell vulnerability, you would first need to launch the msfconsole and search for the proxy shell module. Once you have found it, you can use the "use" command to select it, and then use the "show options" command to view the available options for the module. You would then need to set the required options using the "set" command, and finally use the "exploit" command to execute the payload.
Patching this Vulnerability
While Microsoft has not officially acknowledged the ProxyNotShell vulnerability, they have suggested using third-party web-based protection or Web Application Firewall (WAF) products to implement recommended URL filters and blocks as a precautionary measure. Additionally, limiting outgoing connections or using an outgoing proxy can help to reduce the risk of potentially suspicious web requests. These steps can help to protect against the vulnerability, but it's always important to stay vigilant and keep your software and systems up to date to reduce the likelihood of being exploited
Facts
The ProxyNotShell vulnerability affects on-premise Exchange servers running versions 2013, 2016, or 2019. To exploit this vulnerability, an attacker would need to have authenticated access to the Exchange server. At the moment, there is no patch available to fix this vulnerability. Microsoft has observed attacks using this vulnerability in fewer than 10 organizations globally. These attacks typically involve the use of web shells, which are dropped onto the server by chaining together two zero-day exploits. It's important for organizations to be aware of this vulnerability and take steps to protect themselves.








0 Comments